Researchers from net security company Websense warn that a particular section of the MSN Canada website has fallen victim to hackers who injected rogue code into a page used for redirection. The code is obfuscated and loads content from a domain associated with malware distribution.
The msn.ca website redirects to sympatico.msn.ca, a portal operated by Bell Canada, known for its Internet service provider called Bell Internet, formerly Sympatico, and Microsoft. "Canada's most popular Internet destination," as the website claims of itself, offers all online services available on any MSN portal.
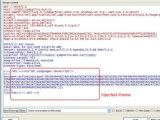
While surfing the website with a packet inspection program on, Jay Liew noticed some strange activity when trying to access cinema.sympatico.msn.ca. The index page on this subdomain is set to redirect users to divertissement.sympatico.msn.ca/Cinema/ via a Location HTTP header. This is also the place where the hackers chose to hide their payload.
"The index page has been infected with obfuscated JavaScript code to redirect users to a known malware host," the Websense researcher explains. The escaped code actually reveals an injected IFrame, which loads content from a remote domain name that has been associated with malicious activities in the past.
The point of entry for this hack has not been revealed, but, according to the company, "Microsoft has since scrubbed the site clean, and we've confirmed that the malicious code is no longer there." The most common Web attacks resulting in code injection are called cross-site scripting (XSS).
XSS weaknesses are the result of poor input validation into web forms and can be persistent, non-persistent, or DOM-based. A persistent cross-site scripting weakness, also known as type 2 XSS, allows for permanent injection of arbitrary code into a page.
Another type of attack, which could have been used to compromise the msn.ca page, even if less likely, is the SQL injection. Such a flaw allows attackers to pass rogue SQL commands with the credentials used by the website via unsanitized parameters.
Fortunately, the hackers made a fatal mistake, which rendered their attack ineffective. According to the Websense analysts, "The Location HTTP header redirects [users] to another MSN Sympatico site before the browser has a chance to render the page and request the malicious content."
Watch Jay Liew explaining the attack on msn.ca:

 14 DAY TRIAL //
14 DAY TRIAL //